CYBER SECURITY FOR CHURCHES
The growth in cyber based crime is increasing, and is fast becoming a key risk for churches, charities and Not-For-Profits to be aware of. Your organisation no doubt relies on email, online banking, social media platforms, apps and other software programs to manage the day to day operation of your ministry. It is time for churches to put cyber risks under the spotlight, be aware of the dangers and minimise the chance of becoming a victim of cyber-crime.
What is Cyber-crime?
Criminal activity carried out using a computer and/or the internet, with the goal of gaining unauthorised access to, or procuring digital information – primarily of a personal or financial nature.
Before implementing strategies to counteract a cyber-attack, let’s first understand the different types of risks, and how they may affect your organisation.

Potential effects of a cyber-attack on your organisation:
- Reputational damage
- Possible breach of Privacy Laws
- Malware shutting down your systems – disrupting business
- Money being transferred to scammers
- Identity theft
- Stealing of data including credit card information, banking details, personal or sensitive information
Cyber criminals will often target organisations such as churches and Not-For-Profits because they tend to have limited resources, making them more vulnerable to attacks.
This, teamed with older computers which haven’t been regularly updated, a large proportion of volunteer staff who may not be well trained in information and data security processes, use of free software programs or cheap web hosting and lack of adequate resources to guard data and defend against cyber-attacks, make for easy targets.
Common Forms of Cyber Attacks on Churches
Social engineering/Phishing Emails
Social Engineering uses deception to manipulate individuals into providing confidential or personal information that may be used for fraudulent purposes.
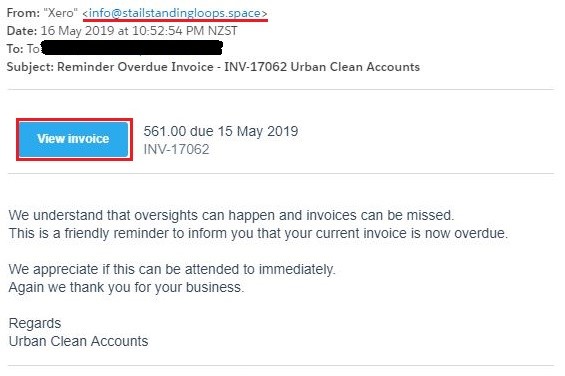
A common example is where a person receives a phishing email which is a clever, authentic looking email aimed at tricking the individual into providing sensitive information or carrying out tasks through deceptive means.
It could include clicking on a malicious link or attachment, or a re-direction to a fake website which requires you to update your details and provide a password.
Quite often the email will look like it comes from a legitimate sender.

Claim Example:
The church treasurer received an email from the Senior Pastor, who was overseas on a mission trip at the time.
The email requested that they transfer $5000 urgently to his bank account as a situation had arisen where the additional funds were required.
The bank BSB and account details were provided in the email.
The email appeared to have come from the Pastor’s email address, the circumstances lined up with the fact that he was overseas at the time, and the request for additional funds was not entirely unreasonable in the situation.
Without any additional checks and balances, the funds were transferred, only to realise later that the Pastor’s email had been hacked, and funds transferred to a cyber-criminal.
Statistics show that 23% of recipients open phishing emails and 11% click on attachments.
How can I tell if an email is a phishing email?
- The message may contain a mismatched URL (hover your mouse over the top of the URL and you should see the actual hyperlinked address. If it is different from the address that is displayed it is probably fraudulent or malicious)
- The email claims to be sent from a senior executive of the business
- The content will have a degree of urgency about it
- The message may contain poor spelling or grammar
- The message asks for personal information (e.g. A password, credit card number or answer to a security question)
In 2017 Australia faced over 10 million cyber-attacks.
Many of these attacks are directed at small businesses or not-for-profits, particularly because their security protocols and systems are less sophisticated than large corporates.
What to do if you receive a phishing email
- Do not respond to the email. Do not click on any of links or attachments in the email.
- If you have an IT Department or Service Provider, forward the email to them to verify
- Delete the email
- Block the sender and warn other recipients
How to avoid becoming a victim of a phishing email or social engineering scam
- Check emailed invoices carefully to ensure that it is a legitimate request for payment. Verify the account directly with the provider (source contact details via a source other than those contained in the suspect email)
- Have clearly defined processes for verifying and paying accounts and invoices. Look very carefully at requests to change banking details.
- Always verify changes to payment details directly with the business or individual using contact numbers previously provided by the vendor/supplier before the request to change was received.
- Ensure that there is a review of all changes to banking records by a second person before a change is processed.
- Never provide your organisations banking, financial or accounting details to unverified parties.
- Train your staff to recognize scam emails.
Malware
Software is used to disrupt computer or mobile operation, gather sensitive information or gain access to a computer. Quite literally – Malware is MALicious softWARE.
10 tips to prevent a Malware attack
- Install Anti-Virus/Malware software – this is a must have first step to keeping your computers virus free.
- Keep Anti-Virus software up-to-date – once you have anti-virus software make sure you maintain it.
- Run regular scans with your Anti-Virus software – set your computers to run regular, scheduled scans (once a week is preferred)
- Keep your operating system current – operating system developers are always issuing OS updates. Just as you would keep your anti-virus software up to date, so to with your operating system.
- Secure your Network – Make sure computers that connect to files, printers or the Internet via a Wi-fi connection requires password access, and that the password is strong. If you regularly have guests who may need to use your Wi-fi connection – provide a specific guest login which provides limited access, and a different password to your main connections.
- Think before you click – don’t open email attachments from unknown sources, don’t click on links in unsolicited email, check URL links by hovering over the link to ensure it is taking you to a legitimate site.
- Keep personal information safe – many hackers will employ social engineering tactics to gather your personal information. Gathering little snippets from various online accounts you may have will enable them to build a bigger picture and potentially steal your identity. Ensure privacy settings are set to high.
- Avoid using open Wi-fi – if you can access it so easily, what can a trained hacker do with the same access?
- Back up your files – back them up to an external hard-drive and keep it in a different location.
- Use multiple strong passwords – Keep it easy to remember but difficult to guess.
Crypto locker
Crypto locker is malware which restricts access to computer files and demands payment in order to be removed and file access restored.

The most common method of infection is via emails with unknown attachments.
These emails can often appear to be from legitimate sources like your bank or workplace.
These types of malware attacks can cause serious damage to personal and business computers.
What to do if your computers are infected with a Crypto locker
- Disconnect your machine from any others and from any external drives – you don’t want the ransomware to spread to other devices on your network
- Use your phone or camera to take a photo of the ransom note that has appeared on your screen
- Contact an expert who can determine if anti-virus or anti-malware software will be able to clean the ransomware from your machine, and potentially recover and restore back up files
- File a Police report – this may be necessary if you intend on making an insurance claim or take legal action. It also assists authorities to keep track of new and emerging threats.
Implement a Cyber Security Checklist for Your Church
- Following are some basic checks to help establish a Cyber Security Check List for your organisation.
- Keep all your software up to date.
- When was it last updated?
- Install a reliable antivirus solution.
- What do we have installed and is it appropriate for our needs?
- Enhance your security with a product that can block attacks antivirus cant detect.
- Use strong passwords. Change them often.
- Can our system automatically prompt staff to update passwords?
- Strong passwords often contain at least 8 characters and use a combination of special characters, numbers and some capital letters. An example would be something like: FrEte@3cyb29
- Activate and use two step verification where available.
- Two step verification is the process of verifying your identity twice using different methods. The most popular method for two step verification is logging in using your email address and a password which then sends a unique code to your phone and only after entering the code correctly gives you access to what you're trying to log into. (more info on two step verification here: https://www.staysmartonline.gov.au/protect-yourself/do-things-safely/two-factor-authentication)
- Avoid oversharing information on social media.
- Does our organisation have a Social Media policy? When was it last reviewed and updated?
- Back up your data. Do it often. Back it up in several places.
- When was data last backed up?
- How often do we back up data?
- Where is data stored?
- Never open emails from unknown senders.
- Are our staff trained to recognise suspicious email communications?
- How is training implemented?
- When was last training/refresher undertaken?
- Never download or open attachment sent from unknown senders.
- Keep financial information safe and don’t share with anyone.
- Who on our staff is authorised to access financial information online?
- Have they been provided with policies and procedures relating to safe processing of online transactions?
- Are requests for changes to bank account details by suppliers checked directly with the supplier, by telephone, with a known contact before amending?
- Avoid untrusted websites and don’t click on suspicious banners or links.
- Adjust privacy and security settings in browsers and apps.
- When were privacy and security settings last reviewed?
- Learn the basics of cyber security and improve your protection.
Resources on Church Cyber Security
The increased frequency and sophistication of these types of cyber-crimes highlights the need for all organisations and individuals to be more vigilant around all manner of online activity.
The Australian Competition and Consumer Commission (ACCC) have a helpful guide The Little Black Book of Scams to assist you to spot, avoid and protect yourself against common scams.
https://www.accc.gov.au/publications/the-little-black-book-of-scams
Up to date information about the latest scams is also available on the Australian Government’s Scamwatch website https://www.scamwatch.gov.au/
You may also wish to subscribe to the Stay Smart Online Alert Service https://www.staysmartonline.gov.au/
Insurance Options
In response to the increased threat of cyber-crime, the insurance industry has developed specific Cyber Liability products which specifically address these types of issues and can provide cover and assistance to deal with these types of claims.
Some of the products already offered by ACS Insurance Services, provide some limited cover for cyber-crimes, but if you are interested in pursuing more comprehensive cover please contact our office, we can advise you of further options that may be available to you.
In our next instalment we will address Privacy Breaches and the new Notifiable Data Breaches Legislation. We will discuss what your organisations obligations are, and the potential risks and penalties if you fail to comply.
DISCLAIMER: The information on this website reflect some of the commercial aspects and potential risks/obligations for your Church, School or Organisation. The information is given as a guide only and does not represent a definitive list or legal view in any way shape or form. You are advised to seek your own professional advice on all your individual needs. ABN: 91 460 778 961 | AFSL/ACL: 247 388

